How to spot and remove malicious Firefox extensions
While the internet offers a plethora of information and services, it also presents various threats. One such threat that often goes unnoticed is malicious browser extensions. These add-ons, while enhancing browser functionality, can sometimes compromise our online security. This guide will help you identify and eliminate malicious Firefox extensions, ensuring a safer browsing experience.
The connection between browser extensions and malware
Browser extensions, engineered to augment browser capabilities and optimize user interaction, may occasionally become vectors for cyber adversaries to disseminate computer malware. The following elucidates the mechanism:
Malicious code injection
Certain browser extensions, either intentionally crafted or subsequently compromised, possess the capability to introduce malevolent code into your browser environment. Upon activation, this code autonomously initiates the download and installation of viruses, malware, or additional undesired software onto your computing system, often bypassing user awareness and consent.
Data theft and phishing
Extensions possessing permissions to access user browsing data have the capability to surveil digital interactions. Extensions with malevolent intent can capture and transmit confidential data, including authentication details, to unauthorized entities. Such acquired data is susceptible to exploitation in deceptive phishing endeavors or identity misappropriation schemes.
Redirects and pop-ups
Some malicious extensions can redirect you to harmful websites or cause unwanted pop-up ads to appear. Among the more notorious culprits are browser hijackers like Search Marquis and Search Baron. These hijackers modify browser settings, redirecting users to specific websites, often filled with ads, to generate revenue for their creators. They can change your homepage, default search engine, or even add unwanted toolbars. Their presence not only disrupts the user experience but can also expose users to additional security risks.
Exploiting browser vulnerabilities
Extensions can sometimes exploit vulnerabilities in the browser itself, allowing viruses to bypass security measures and gain access to your system.
Recognizing Malicious Extensions
Common signs of malicious extensions
Unexpected pop-up ads, a changed homepage, or a sudden decrease in browser performance can all be indicators of a malicious extension. These extensions can pose significant threats, from being mere nuisances to serious security risks, such as data theft, online tracking, or redirection to phishing sites.
Why do people create malicious extensions?
The primary motive behind most cyber threats, including malicious extensions, is profit. Cybercriminals deploy these extensions to steal personal data, inject ads into websites, or even create botnets for larger cyber-attacks.
Steps to spot malicious extensions
Reviewing extension permissions
Before installing an extension, it's crucial to scrutinize the permissions it requests. An extension's permissions should align with its functionality. For instance, a wallpaper extension shouldn't need access to your browsing history.
Checking extension reviews and ratings
The Firefox community is a valuable resource when assessing an extension's credibility. User reviews and ratings can provide insights into the extension's performance and trustworthiness. An extension with numerous complaints or low ratings is a potential red flag.
Researching the extension developer
The developer behind an extension can offer clues about its legitimacy. Established developers with a track record of producing reliable extensions are generally more trustworthy. However, many extensions are developed by lesser-known individual developers. In such cases, it's beneficial to check the developer's website, blog, or social media activity to see if it aligns with the extension's features.
Understanding permissions and their relevance
When an extension requests permissions, it's essential to understand why. If an extension asks for your location, its description should justify this request. If the reasons for certain permissions aren't clear, the extension's website or its page on addons.mozilla.org should provide an explanation. Always ensure that the given explanation aligns with the extension's features.
Privacy policies and data handling
An extension's approach to data privacy is crucial. Does the extension have a clear privacy policy? If so, are you comfortable with how your data will be collected and used? Understanding and being comfortable with an extension's data practices is essential before installation.
How to remove malicious extensions
Step-by-step guide to get rid of extensions from Mozilla Firefox:
- Open Firefox.
- Click on the hamburger menu in the top right corner.
- Select Add-ons and themes or use the shortcut Ctrl+Shift+A.
- Browse through your list of extensions to find the suspicious one.
- Click Remove.
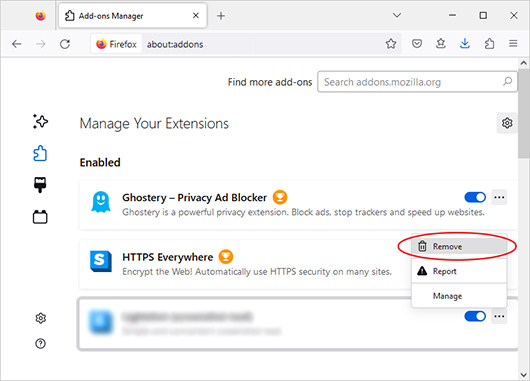
- Restart Firefox to ensure the changes take effect.
After removing a potentially harmful extension, it's advisable to clear your browser's cache and cookies. This step ensures that any residual data or settings from the malicious extension are completely eradicated.
Protecting your browser in the future
Regularly update
Keeping your browser updated is a simple yet effective way to enhance security. Updates often patch known vulnerabilities, ensuring you're protected against them.
Use trusted extension sources
While exploring extensions, it's safest to stick to official sources like the Firefox Add-ons site. These platforms vet extensions for security, ensuring a reduced risk of encountering malicious ones.
Mozilla's recommended extensions
Mozilla has an official list of extensions that they endorse through the Recommended Extensions program. These extensions have undergone rigorous checks and are deemed safe for use. Checking this list can provide users with additional confidence in their extension choices.
Safe browsing is a continuous effort
The digital realm is dynamic, with new threats emerging daily. However, by staying informed, practicing vigilance, and following best practices, you can ensure a secure and enjoyable online experience.